Data Security (version 23)
The following article describes how data is secured
- In transit from Collector to Historian
- At rest in the Historian
- When accessed from the Historian
Security In Transit
Each Canary Collector is paired with a Sender service responsible for forwarding (and buffering) the data to the Receiver service and the Historian. A TCP connection is made between Sender and Receiver wherein binary packets of data are sent. There are two ports on which the Receiver listens: 55255 (anonymous) and 55256 (secure). By default, the Sender attempts to connect to the anonymous port. If this port is unavailable or disabled, it will attempt to connect to the secure port. When connecting to the secure port, the binary packets are encrypted using TLS. Additionally, the Sender client must be manually allowed on the Receiver's access list before data can flow through freely.
Security At Rest
Once data arrives at the historian, it is stored within a DataSet in hdb2 files. These files are proprietary and can only be read using Canary software. It is important to note that these files are not encrypted. If wishing to encrypt the data at rest, the volume on which the data resides must be encrypted.
Security When Data is Accessed
The Views service acts as the gateway for clients wishing to access and consume data from the Historian. Whether connecting with Axiom, the Excel Add-in, the Read API, or the ODBC connector, all clients are routed through Views. As such, any user/group wishing to connect must be given access on Views' ALLOW list.
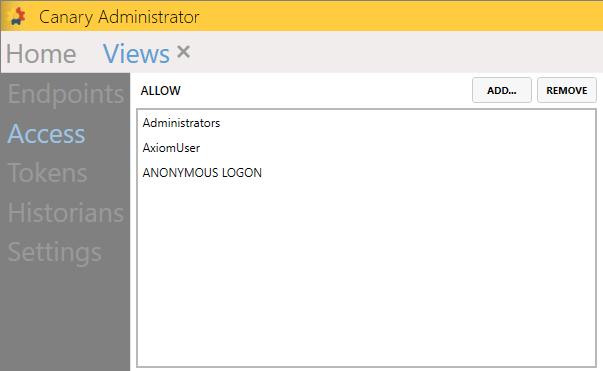
Furthermore, once access is provided, security can be enabled through the Views>Security tab to control what data the user/group has access to. It may be that you want to limit what data is visible to the end user. See Applying Security to Views.
Similar to the Receiver, the Views service offers both anonymous and secure TCP endpoints to connect to. Data is encrypted with TLS when connecting to the secure endpoints.
