How to Add an OpenID Connect Identity Provider (version 25)
By default, Canary uses Windows AD for user authentication; however, Canary also supports OAuth 2.0/OpenID Connect. This gives end users alternate options for signing into Canary's application tools (Canary Admin, Axiom, and Excel Add-in) while supporting SSO. Below are some examples of supported OpenID Connect providers:
- Entra ID (Azure)
- Microsoft AD Federation
- Okta/Auth0
- Customer-Defined OAuth Providers
To add an OpenID Connect provider, the following steps can be taken. In this example, we are adding an Entra ID provider. Parameter names and configuration may vary depending on the provider.
- Open the Canary Admin and navigate to the Identity tile>Configuration>Providers screen.
- Click ADD in the OPENID CONNECT PROVIDERS section.

- Fill in the Provider Display Name, Provider URL, Client ID, and Client Secret as provided by the identity provider. The Provider Display Name does not need to match anything coming from the provider, but should be intuitive. In this example, we are just calling it Azure.

Use the OpenID Connect metadata document URL for the Provider URL. Remove "/.well-known/openid-configuration" from the end of the URL.
Use the Application ID for the Client ID.
A new client secret should be created for the Identity service within the IDP. Use the Value for the Client Secret.
- Click ADD and apply changes.
- Add a Redirect URI to point the identity provider back to the Identity service on the Canary server (e.g. https://canaryServerName:55353/oidc/callback/login/providerDisplayName). This redirect URI will be used specifically for the Excel Add-in and Canary Admin client. Axiom will use a separate redirect URI created in the next step.

- Add a Redirect URI for Axiom. Starting in v25, Axiom utilizes a reverse proxy which allows the Identity service to use the same port as Axiom, 443, to communicate with the Identity service. (e.g. https://canaryServerName/identity-proxy/oidc/callback/login/providerDisplayName)

- Create a group claim for the app registration and enable Security groups.
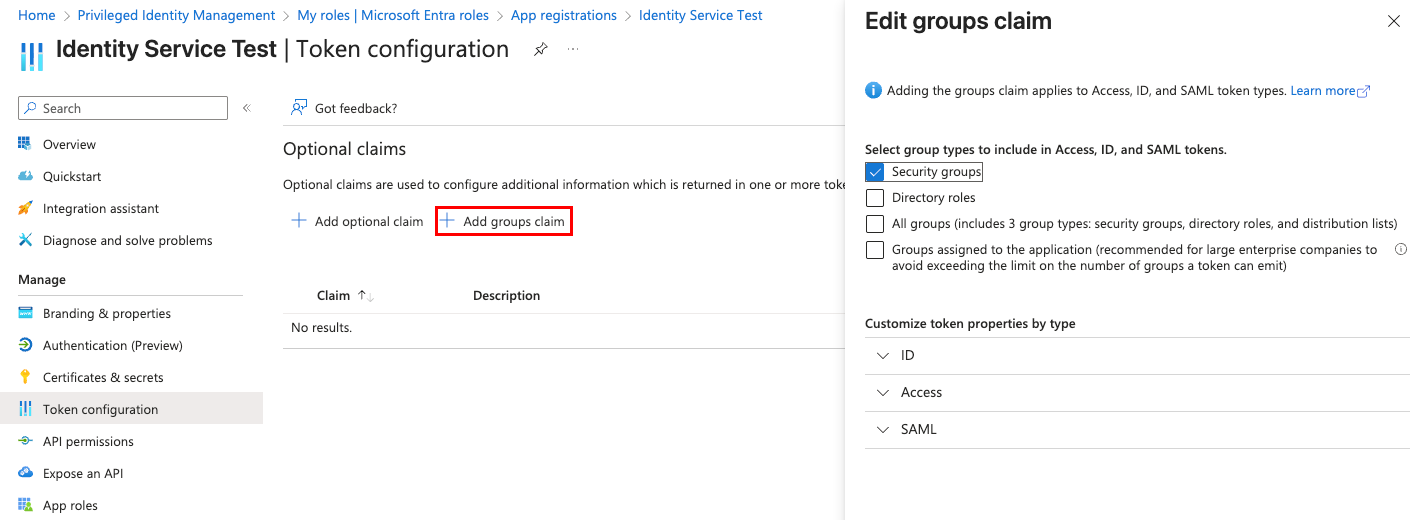
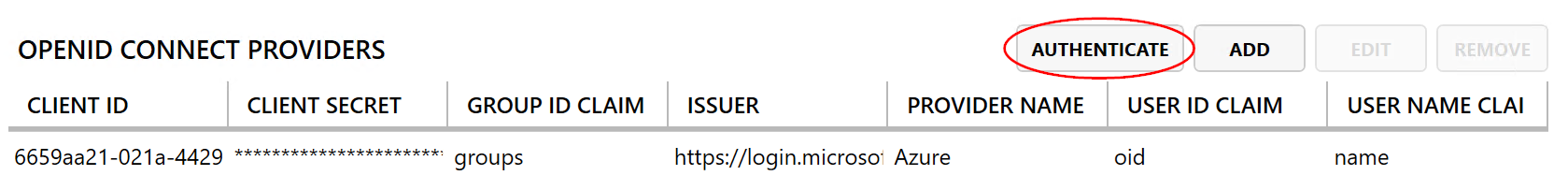
- Navigate back to the Identity tile and click AUTHENTICATE.
If the information is correct, the following message should appear:
- Navigate to the Messages tile and look for the following Info message at the top of the list. This will contain the claims that are needed to complete the OpenID Connect provider.

- Navigate back to the Identity tile and EDIT the newly created OpenID Connect provider.
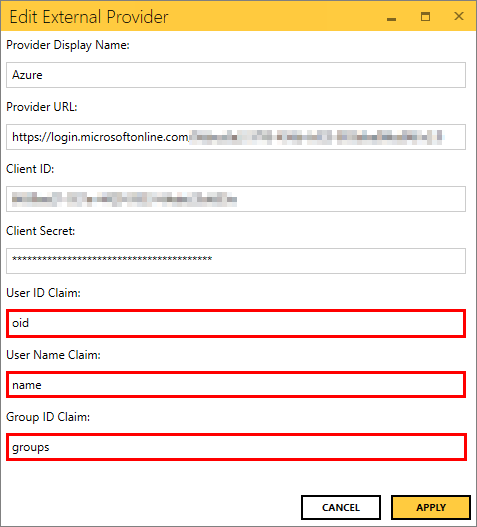
- Fill in the User ID Claim, User Name Claim, and Group ID Claim using the claim labels (not claim ID's) from the message then click APPLY.
Once configured, the user will see the available option when logging into the Canary Admin, Axiom, or the Excel Add-In.

If wishing to then disable Windows AD, uncheck the box 'Enable Active Directory' within the Identity tile>Configuration>Providers screen.
4 replies
-
What is the application being used for "Identity Service Test"?
-
Note that in steps 9 & 10 above, when entering the claims to complete the OpenID Connect provider, you must use the actual label for the claim, and not the claim IDs. For example, for the User ID Claim, you must enter "oid" (without the quotes), for User Name Claim, enter "name" (without quotes), and for Group ID Claim, enter "groups" (without the quotes).
