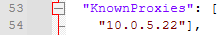Identity Provider Routing (version 25)
Identity Provider Routing is used to control which identity providers (e.g. Active Directory, Anonymous, OpenId Connect provider, etc.) are available to end-users logging in based upon their IP address. It may be that you want expose a certain provider to users from one subnet and a different provider to users from another subnet. If so, the following settings must be configured.
Configuration
The "IdentityProviderRoutes" setting can be configured in the %ProgramData%/Canary/Identity/identity.service.json file. After making changes to the file, restart the Identity service for the changes to take effect. Here is an example of routing configuration:

"IdentityProviderRoutes": [
{
"IpAddressRegex": "^(::ffff:)?10\\.0\\.3\\.35$",
"ProviderNameRegex": null
},
{
"IpAddressRegex": null,
"ProviderNameRegex": "(Active Directory|Anonymous)"
}
],
Each route has two regular expressions. If the IP address of the client matches on the IpAddressRegex expression, then any providers matched by the ProviderNameRegex expression will be displayed to the client. If either expression is null, that means "match anything".
The provider names that are matched against the ProviderNameRegex expression are the same provider names that appear in the Identity login page (except for "Anonymous" instead of "Anonymously"):

Regex Tips
A good pattern for ProviderNameRegex is to use "(provider one|provider two|provider three)". The pipe character separates the provider names which will be allowed by this route. More advanced regex could be used, but it is not likely to be very useful.
For IpAddressRegex, we used the pattern ^(::ffff:)?10\\.0\\.3\\.35$. Note the IPv4 address 10.0.3.35 at the end. You can use this general pattern to match on a particular IPv4 address. (::ffff:)? at the front of the expression allows this to work when it's an IPv6 mapped IPv4 address.
Behavior
If there are no routes configured, then all of the providers will be available from any IP address.
Routes are evaluated in order. The first route that matches the IP address of the client is used, and only the providers matched by that route will be available to the client.
If only one provider is available to a client, the browser will bypass the "select an Identity provider" page.
If no providers are available to a client, an error page will be displayed.
Additional Configuration for Proxies and Load Balancers
If the Identity service is running behind a load balancer or proxy (including the Axiom Reverse Proxy), the following configuration changes are needed to support Identity Provider Routing.
Proxy/Load Balancer
The proxy/load balancer needs to send an "X-Forwarded-For" header to Identity with the client's IP address. Axiom does this automatically, but other load balancers such as Nginx will need to be configured to send this header.
Identity Service
The IP address(es) of the proxy/load balancer need to be added to the "KnownProxies" array in the identity.service.json file. If the proxy server may connect to Identity with both IPv4 and IPv6 addresses, then both addresses should be added to the file.